Operation Darknet
Confirmed 231,082
Part of a series on Anonymous. [View Related Entries]
Operation Darknet
Part of a series on Anonymous. [View Related Entries]

Overview
Operation Darknet (also known as #OpDarknet) is the codename for a series of distributed denial-of-service (DDoS) attacks carried out by Anonymous on Lolita City, a child pornography sharing website that is accessible in anonymity via The Tor Project's encrypted service. This campaign is not to be confused with two earlier Anonymous operations that have shared the same name, one from January 2010[19] to provide a solution to the censorship threatened by the ACTA (Anti-Counterfeit Trade Agreement) and another initiative from April 2011[1] to inform Anonymous members to start using I2P to protect their anonymity.[2]
Background
The operation began in early October 2011 with a mission to expose the underground pedophile community known as "Lolita City." The website was built via Tor[3], a software that allows users to host and browse websites anonymously. Built to protect the anonymity of Internet users under regimes that do not allow free internet access, the program has seen its use in least four other forum communities accused of hosting child porn, as well as a drug marketplace known as "Silk Road" where users could buy illegal drugs with Bitcoins.[4]
Notable Developments
October 14th – 15th: PasteBin Release
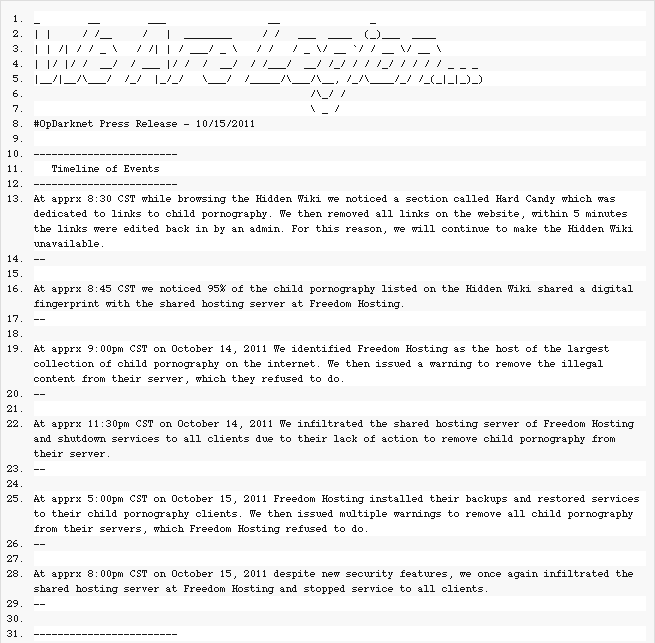
The major events of the Operation took place between October 14th and 15th, as archived in a Pastebin[5] document. On October 14th, Anonymous hackers began their mission by removing links to pornographic images and videos on the Hidden Wiki, located on Tor's Hidden Service Protocol.[6] Shortly after the links returned online, the site became inaccessible in its entirety, presumably as a result of DDoS attack initiated by the group.
October 15th: Target Freedom Hosting
Following the initial attack, Anonymous members found out nearly all of the pornography had the Freedom Hosting digital fingerprint and thus issued the host a warning to remove the content from its server at 9 p.m. (CST) on October 14th. Freedom Hosting refused to comply and two and a half hours later, Anonymous completely shut down Freedom's services with DDoS attacks that created a 1GB SQL and 100,000 ASCII files of Guy Fawkes masks every five minutes.[7]

Around 5 p.m. (CST) the next day, Freedom was able to restore service completely via backup servers. Anonymous issued several additional warnings to the company, giving them 3 hours before taking down the server again, this time using an attack codenamed "Chris Hanson," which uploaded episodes of "To Catch a Predator" labeled as "CP" on to the site.

October 17th: Anonymous Releases Communique
On October 17th, YouTuber BecomeAnonymous[8] uploaded a video with the Anonymous manifesto, explaining the motivations behind Operation Darknet and its future plans.
October 18th: Userbase Exposed
On October 18th, Anonymous released the names of the 1589 users of Lolita City via PasteBin[9], including their username, volume of images uploaded, and age of the account. They invited Interpol and the FBI to investigate the records further.
October 20th – 24th: News Media Coverage
News of the operation spread quickly, with the earliest news story appearing on the Examiner[10] on October 20th, Gawker[4] on the 21st, the Huffington Post[11] and PC World[12] on the 22nd, and Geekosystem[13] on the 23rd. The Examiner story was shared on Reddit[18] on October 22nd, where it received 2475 points in two days.
By October 24th, the news had reached the Wall Street Journal[14], Information Week[15], and the BBC.[16] Techie Buzz[17] also published an interview with a user named "arson" in the #OpDarknet IRC channel. Arson stated that their mission was only to take down illegal materials and the operation was not triggered by any particular event:
We vowed to fight for the defenseless, there is none more defenseless than innocent children being exploited.
November 2nd: Final Release
The last official PasteBin[20] communique from #OpDarknet was uploaded on November 2nd, 2011. They stated that the whole plan behind the operation was not to take down Tor or the darknet in general, but specifically to attack the CP sharing occurring on these sites. It revealed "The Honey Pawt," a modified TorButton for Firefox, which, when used, would log users information if they tried to access the Hard Candy wiki or Lolita City.
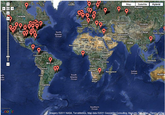
On October 27th, Operation Paw Printing went into effect for 24 hours, marking the end of the DDoS attacks on The Hidden Wiki and implementation of the modified TorButton, which was only available on the Hard Candy page. When a user of HC updated the button, their IP information was logged. Over the course of the day, 190 unique users and IP addresses were logged, mapped out below.

The PasteBin document noted that November 5th, 2011, Guy Fawkes Day, would mark the end of the Operation and Anonymous would be "sailing away for another Lulz."
February 2017: Freedom Hosting II Hacked
On February 3rd, 2017, an Anonymous-affiliated hacker infiltrated the servers of Freedom Hosting II, a controversial web hosting service that reportedly hosts 20% of sites on the Dark Web, and claimed to have shut down 10,613 child pornography and online scam websites in a message posted on some of the compromised websites. Featuring the signature tagline "we are Anonymous / we do not forgive / we do not forget," the message also revealed that all of the hosted files have been copied and the database has been wiped, while offering to sell the data back to Freedom Hosting II in exchange for 0.1 bitcoin (appx. $100).

click through for the transcript
On February 4th, VICE Motherboard[24] ran an interview with one of the hackers behind the Dark Web crackdown, who told the reporter that it was their "first hack ever" and they intend to hand over the user data to a security researcher for further investigation by law enforcement.
Search Interest
Though Lolita City has had consistent search hits, there is a huge spike in October 2011, coinciding with the Operation.
External References
[1] PasteHTML – #OpDarknet
[2] CyberGuerrilla – Anonymous – Press Release 4/26/2011 – OPERATION DARKNET #OpDarknet
[4] Gawker – https://gawker.com/5851459/vigilante-hackers-wage-war-on-underground-kiddie-porn
[5] PasteBin – #OpDarknet Major Release & Timeline
[6] Ars Technica – Anonymous takes down darknet child porn site on Tor network
[7] PasteBin – #OpDarknet – To Catch A Predator
[8] YouTube – Become Anonymous
[9] PasteBin – #OpDarknet – Lolita City user dump
[10] Examiner (via Wayback Machine) – Anonymous exposes pedophile ring – hacks Lolita City
[11] Huffington Post – Anonymous Hacks Lolita City Alleged Porn Ring
[12] PC World – Hacker Collective Anonymous Strikes at Child Porn Sites
[13] Geekosystem – Anonymous Takes Down Massive Child Pornography Server, Leaks Usernames
[14] The Wall Street Journal – Anonymous Hacktivists Target Child Pornography Sites
[15] Information Week (via Wayback Machine) – Anonymous Attacks Child Pornography Websites
[16] BBC – Hackers take down child pornography sites
[17] Techie Buzz – An Interview with an OpDarknet Anon
[18] Reddit – Anonymous exposes pedophile ring
[19] Anonymous Hamburg – AnonyNEWS – KW4
[20] PasteBin – #OpDarknet – Paws Up: A Sticky Situation
[21] The Verge – An Anonymous group just took down a fifth of the dark web
[22] Twitter – @SarahJamieLewis' Tweet
[23] Telegraph – Anonymous hacker knocks 20pc of dark web offline in campaign against child pornography
[24] VICE – We Talked to the Hacker Who Took Down a Fifth of the Dark Web
Recent Videos 3 total
Recent Images 9 total
Share Pin












Top Comments
Skitch the Wolf, KYM Community Pet
Oct 24, 2011 at 08:41PM EDT
Cyber6x Moderator
Oct 25, 2011 at 04:41AM EDT