
Overview
Cicada 3301 is an annual online scavenger hunt in which the participant is asked to complete a series of complex and interconnected puzzles using various clues embedded in multimedia files. Purportedly designed to recruit "intelligent individuals" and heavily focused on data security, cryptography, and steganography, the mysterious puzzle-solving challenge has garnered considerable attention on the web since its launch in January 2012.
Background
The contest began on January 4th, 2012, when an image of a text-based puzzle was posted to 4chan's /b/ (random) and /x/ (paranormal) boards, which challenged the readers to find a hidden message in the file (shown below).

The mysterious post was quickly met by various speculations and theories surrounding its true intent, with some simply interpreting the message as yet another alternate reality game (ARG), while others suspected that it was a recruitment program for the United States intelligence community.
Notable Developments
The following account is a summary report of all known discoveries concerning Cicada 3301 based on the information provided by the Wikia project Uncovering Cicada.[1]
2012
The first clue in the puzzle was retrieved by opening the image file in a text-editing application, which revealed the following message encoded as a Caesar Cipher:
TIBERIVS CLAVDIVS CAESAR says "lxxt>33m2mqkyv2gsq3q=w]O2ntk"
Upon decrypting, the text revealed a URL address to an image of a wooden duck accompanied by another cryptic message (shown below), which vaguely suggested the use of OutGuess, a steganography application used to hide and find messages within image files. Once processed through the program, the file unlocked a link to /r/a2e7j6ic78h0j, a mysterious Reddit community populated with two additional images and a series of text posts encrypted in codes.

After being processed through OutGuess, the two images revealed the following messages:
"From here on out, we will cryptographically sign all messages with this key. It is available on the mit keyservers. Key ID 7A35090F, as posted in a2e7j6ic78h0j. Patience is a virtue."
The key has always been right in front of your eyes. This isn't the quest for the Holy Grail. Stop making it more difficult than it is. Good luck. 3301
Using the numeric sequence displayed in the header section of /r/a2e7j6ic78h0j as the "key" (10, 2, 14, 7, 19, 6, 18, 12, 7, 8, 17, 0, 19, 7, 14, 18, 14, 19, 13, 0, 1, 2, 0), each letter in the ciphers were then shifted by the number corresponding to its location in the text. The shifting method revealed the text of Owain, or the Lady of the Fountain, one of the three tales associated with the Middle Welsh proses known as the Mabinogion.
The text could be then decoded using the book code, a type of cipher in which the first number is the line and the second number is the character in that line. The deciphered message read:
Call us at us tele phone numBer two one four three nine oh nine six oh eight
Upon dialing this phone number (214 – 390 – 9608), a pre-recorded message was played:
Very good. You have done well. There are three prime numbers associated with the original final.jpg image. 3301 is one of them. You will have to find the other two. Multiply all three of these numbers together and add a .com to find the next step. Good luck. Goodbye.
After multiplying the 3301 with the width and height of the original image (509 pixels by 503 pixels), both of which are prime numbers, the sum revealed the following domain:
https://845145127.com
You have done well to come this far. Patience is a virtue. Check back at 17:00 on Monday, 9 January 2012 UTC. 3301
Upon running the same image through OutGuess for the second time, a new message was produced with a series of GPS co-ordinates in addition to the two sets already provided on the website (shown below).

Main IRC channel on n0v4. At each of these locations, brave solvers found a sheet of paper stuck to a telegraph pole, with a QR code and an image of a cicada. It took a while for this to sink in with the community, that this wasn't just a talented neckbeard in a basement, that this was actually a global organisation of some very very talented people.
2013
On January 5th, 2013, a second instruction file named "232.jpg" was posted to /x/ and /b/ boards on 4chan. For more detailed information, please read What Happened over at Uncovering Cicada.

2014
On January 5th, 2014, @1231507051321, the Twitter account known to be affiliated with the project, tweeted a link to an Imgur-hosted instruction. For more information on the latest progress, please read What Happened over at Uncovering Cicada.

2015
No new activity was heard from Cicada 3301 nor was there any puzzle reveal from the group in 2015 other than a Pastebin message tweeted from the @1231507051321 Twitter account on July 28th denying any involvement in illegal activities against health organization Planned Parenthood after a number of cyber attacks from an unaffiliated group also calling themselves 3301 and that they "are not associated with this group in any way, nor do condone their use of our name, number, or symbolism."[19]
2016
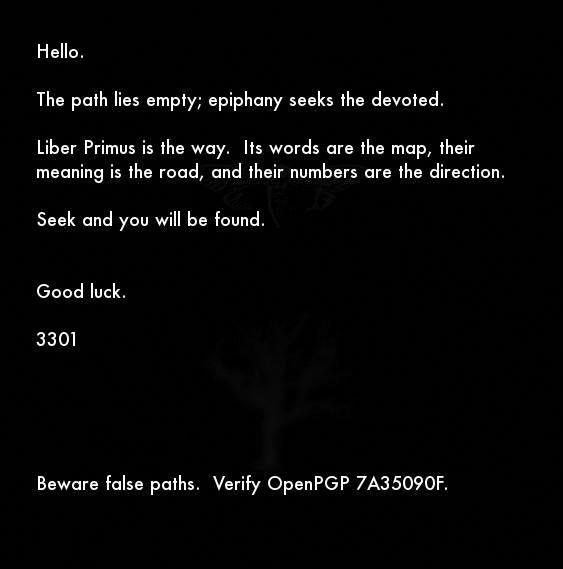
On January 5th, 2016, the @1231507051321 Twitter account tweeted a link to an image hosted on the service Infotomb containing an instruction file encouraging the decoding of the Liber Primus, an image dump of 58 pages given out in May of 2014 to followers of the event via an .onion link. The pages can be seen here and more information can be read at What Happened Liber Primus over on Uncovering Cicada.
Media Coverage
In January 2012, shortly after the introduction of the first cipher, the mysterious event was blogged about by several participants attempting to crack the codes, eventually leading to discussion threads on dozens of online forums and websites. The earliest known coverage of Cicada 3301 from a major news outlet came from the Telegraph in a November 2013 article titled "The Internet mystery that has the world baffled," which included quotes from Joel Eriksson, a 34-year-old Swedish computer analyst and cryptographer participating in the challenge. In December 2013, WNYC ran a story about "Tekk.nolagi," a San Francisco teenager who solved the puzzle in collaboration with a 10-person team known as "#decipher." In early January 2014, as the anticipation began to build up for the third annual event, Cicada 3301 was reported on by a slew of well-known news publications, including the NPR, CBS and The Independent.
Search Interest
External References
[1] Wikia – Uncovering Cicada
[2] Wikia – What Happened Part I
[3] Mental Floss – Chasing the Cicada: Exploring the Darkest Corridors of the Internet
[4] Pastebin – Here is a book code
[5] Reddit – /r/a2e7j6ic78h0j
[6] The Belfast Telegraph – Masonic conspiracy or MI6 recruitment tool? Internet mystery Cicada 3301 starts up again
[7] Wikipedia – Cicada 3301
[8] CBS News – Is this a clue for online code-breaking scavenger hunt Cicada 3301?
[9] The Telegraph – Cicada 3301 update: the baffling internet mystery is back
[10] I Started Something – “Cicada 3301″ cryptographic puzzle game played out on 4chan & reddit: best job hire in disguise?
[12] GitHub – Cicada 3301 wiki
[13] The Telegraph – The internet mystery that has the world baffled
[14] XKCD – Cicada / 3301 – Crazy International Internet/Crypto Mystery
[15] 4chandata – somebody can explain me that cicada 3301 thing?
[16] NPR – The Internet's Cicada: A Mystery Without An Answer
[17] Twitter – 1231507051321's Feed
[18] Twitter – 1231507051321's Tweet





















Top Comments
Slapperfish
Jan 08, 2014 at 08:12PM EST
Fartingo
Jan 08, 2014 at 08:01PM EST