Heritage Foundation Gay Furry Hack
Submission 7,570
Part of a series on Hacktivism / Internet Vigilantism. [View Related Entries]
Related Explainer: Who Are The 'Gay Furries' That Hacked The Heritage Foundation? The Hacktivist Group 'SiegedSec' Explained
Heritage Foundation Gay Furry Hack
Part of a series on Hacktivism / Internet Vigilantism. [View Related Entries]
This submission is currently being researched & evaluated!
You can help confirm this entry by contributing facts, media, and other evidence of notability and mutation.
Overview
Heritage Foundation Gay Furry Hack refers to a hacktivist group's leak of internal data from the conservative United States think tank the Heritage Foundation in mid-July 2024. A self-professed group of "Gay Furry Hackers" took credit for the leak on their Telegram channel, where they notably call themselves "SiegedSec." The group has taken credit for a series of hacks and leaks targeting conservative American groups in 2024.
Background
On July 9th, 2024, SeigedSec, a self-described gay furry hacktivist group, posted about hacking and leaking internal data from the Heritage Foundation, a conservative American think tank based in Washington, D.C., to their Telegram[1] channel called "SiegedSecurity" (seen below). The think tank is best known for its work on the controversial Project 2025 campaign.
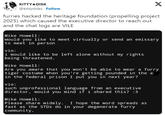
Images from the data dump were reposted to X[2] by user @ZachTheW0lf on July 9th, gathering over 48,000 likes in two days.


Developments
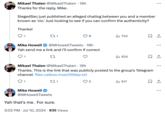
On July 10th, 2024 SeigedSec posted a Signal chat log[3] between the Heritage Foundation's Mike Howell and the group behind the hack. The chats show the hacker and Howell exchanging words, with Howell threatening to expose the furry's real identities and calling them "degenerate perverts" (shown below).


The validity of these chats was later confirmed by journalist Mikael Thalen[4] in a public correspondence with Mike Howell on July 10th (seen below).

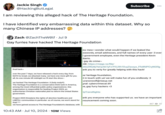
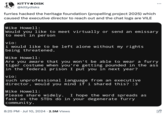
Also on July 10th, 2024, X[5] user @HackingButLegal posted a thread analyzing some of the data leaked by SeigedSec, concluding that several comments on the Heritage Foundation's website originated from Asian countries (seen below).
![Heritage Foundation Gay Furry Hack Jackie Singh @HackingButLegal • 22h Dataset was a little dirty and a hassle to clean up. Here are the 60K extracted IPs from the WP Comments table: defuse.ca/b/ PTrmvlbs #HeritageFoundation ge grep -oE '\b([0-9]{1,3}\.){3}[0-9]{1 5] 12[0-4][0-9] | [01]?[0-9][0-9]?)\.){3} 0-9]?)$/!d' > output.txt 6 1785 1.1K III 216K Jackie Singh @HackingButLegal Subscribe Sample geolocations from the first 100 IPs (these are sorted 'low to high', and many Asia-based netblocks start with the number 1) Checking... #: 26/100 74 to go IP Address Reverse DNS Country Region • City Zip Code Timezone ISP 1-172-10-38.dynamic- Penghu | Penghu 1.172.10.38 Taiwan Asia/Taipei Chunghwa Telecom Co., Ltd. ip.hinet.net County County 1-172-15-59.dynamic- Penghu 1.172.15.59 Taiwan ip.hinet.net County | Penghu County Asia/Taipei Chunghwa Telecom Co., Ltd. 1.186.48.26 1.186.48.26 India Karnataka 1.207.26.87 1.207.26.87 China Guizhou 1.23.84.39 1.23.84.39 India West Bengal Kolkata Bengaluru 560056 Asia/Kolkata Guiyang 550000 Asia/Shanghai 700014 Asia/Kolkata DVOIS Chinanet Tikona Infinet Ltd. South 1.234.27.239 1.234.27.239 Seoul Seocho-gu 066 Asia/Seoul SK Broadband Co Ltd Korea 1.24.119.19 1.24.119.19 China Fujian Zhangzhou Asia/Shanghai China Unicom Neimeng Province Network South 1.251.19.135 1.251.19.135 Daegu Seo-gu 418 Asia/Seoul SK Broadband Co Ltd Korea 1.26.102.189 1.26.102.189 China Fujian Zhangzhou Asia/Shanghai China Unicom Neimeng Province Network 1.53.161.195 1.53.161.195 Vietnam Ho Chi Minh | Quan Binh Thanh 1.55.89.216 1.55.89.216 Vietnam Hanoi Hanoi 1.55.95.220 1.55.95.220 Vietnam Hanoi Hanoi 1.59.151.107 1.59.151.107 China Heilongjiang Harbin 1.61.122.87 1.61.122.87 China Heilongjiang Harbin 150000 Asia/Shanghai 1.62.83.6 1.62.83.6 China Heilongjiang Harbin 150000 Asia/Shanghai Asia/Ho Chi Minh FPT Telecom Company Asia/Bangkok Asia/Bangkok 150000 Asia/Shanghai FPT Telecom Company China Unicom Heilongjiang Province Network China Unicom Heilongjiang Province Network China Unicom Heilongjiang Province Network FPT Telecom Company 1-64-176- 1.64.176.95 Hong Kong Eastern 095.static.netvigator.com Heng Fa Chuen Asia/Hong_Kong PCCW IMS Limited 1-64-55- 1.64.55.226 Hong Kong Eastern 226.static.netvigator.com Metropole Building 96521 Asia/Hong_Kong PCCW IMS Limited 12:03 PM ⚫ Jul 10, 2024 250K Views](https://i.kym-cdn.com/photos/images/newsfeed/002/859/063/865.png)
![Heritage Foundation Gay Furry Hack Jackie Singh @HackingButLegal Here's an example of the fun we can have here: Subscribe Match suspicious comments to suspicious IP addresses. Here we have "Clint" who asks, "I am not sure who told you that 'Space-based interceptors present the best option for a boost-phase missile defense.' Can you point me to a technical study? This Air Force (ex-AF) officer says the opposite is true: that space based missile defense is not feasible [links] So I am confused it seems space based missile defense is not the most sensible thing to do. If you have any other information to share on this issue that would be good. Thanks." "Clint" made this particular comment from an IP address originating from Kathmandu, Nepal. e_i@yahoo.com', whois: status: ALLOCATED II '110. ' whois.apnic.net 2008-11 IANA sure who told you that & changed: missile defense." Force (ex-AF) officer say ible: \n <a href="http: .thespacereview.com/artic href="http://www.missile llow">http://www.missilet seems space based missile r information to share on 0, 0), 12:21 PM ⚫ Jul 10, 2024 355.1K Views source: #whois.apnic.net % [whois.apnic.net] % Whois data copyright terms http://www.apnic.net/db/dbcopyright.html % Information related to '110.34.4.0 110.34.4.255' % Abuse contact for '110.34.4.0 110.34.4.255' is 'abuse@subisu.net.np' inetnum: netname: descr: country: admin-c: tech-c: abuse-c: status: mnt-by: mnt-irt: last-modified: source: irt: address: address: address: e-mail: abuse-mailbox: 110.34.4.0 110.34.4.255 SUBISU Corporate_Pool17 SUBISU Corporate_Pool17 NP ATC1-AP SA1-NP AS2579-AP ASSIGNED NON-PORTABLE MAINT-NP-SUBISU IRT-SUBISUCABLENET-NP-NP 2021-02-02T16:05:26Z APNIC IRT-SUBISUCABLENET-NP-NP PO Box: 6626, Baluwatar Kathmandu Nepal engg@subisu.net.np abuse@subisu.net.np](https://i.kym-cdn.com/photos/images/newsfeed/002/859/069/9ce.png)
SiegedSec also announced that they were disbanding in their Telegram[1] channel on July 10th following the leaks.
Search Interest
External References
Recent Videos
There are no videos currently available.
Recent Images 13 total
Share Pin
Related Entries 11 total
Recent Images 13 total
Recent Videos 0 total
There are no recent videos.
![Heritage Foundation Gay Furry Hack Jackie Singh @HackingButLegal Here's an example of the fun we can have here: Subscribe Match suspicious comments to suspicious IP addresses. Here we have "Clint" who asks, "I am not sure who told you that 'Space-based interceptors present the best option for a boost-phase missile defense.' Can you point me to a technical study? This Air Force (ex-AF) officer says the opposite is true: that space based missile defense is not feasible [links] So I am confused it seems space based missile defense is not the most sensible thing to do. If you have any other information to share on this issue that would be good. Thanks." "Clint" made this particular comment from an IP address originating from Kathmandu, Nepal. e_i@yahoo.com', whois: status: ALLOCATED II '110. ' whois.apnic.net 2008-11 IANA sure who told you that & changed: missile defense." Force (ex-AF) officer say ible: \n <a href="http: .thespacereview.com/artic href="http://www.missile llow">http://www.missilet seems space based missile r information to share on 0, 0), 12:21 PM ⚫ Jul 10, 2024 355.1K Views source: #whois.apnic.net % [whois.apnic.net] % Whois data copyright terms http://www.apnic.net/db/dbcopyright.html % Information related to '110.34.4.0 110.34.4.255' % Abuse contact for '110.34.4.0 110.34.4.255' is 'abuse@subisu.net.np' inetnum: netname: descr: country: admin-c: tech-c: abuse-c: status: mnt-by: mnt-irt: last-modified: source: irt: address: address: address: e-mail: abuse-mailbox: 110.34.4.0 110.34.4.255 SUBISU Corporate_Pool17 SUBISU Corporate_Pool17 NP ATC1-AP SA1-NP AS2579-AP ASSIGNED NON-PORTABLE MAINT-NP-SUBISU IRT-SUBISUCABLENET-NP-NP 2021-02-02T16:05:26Z APNIC IRT-SUBISUCABLENET-NP-NP PO Box: 6626, Baluwatar Kathmandu Nepal engg@subisu.net.np abuse@subisu.net.np](https://i.kym-cdn.com/photos/images/list/002/859/069/9ce.png)
![Heritage Foundation Gay Furry Hack Jackie Singh @HackingButLegal • 22h Dataset was a little dirty and a hassle to clean up. Here are the 60K extracted IPs from the WP Comments table: defuse.ca/b/ PTrmvlbs #HeritageFoundation ge grep -oE '\b([0-9]{1,3}\.){3}[0-9]{1 5] 12[0-4][0-9] | [01]?[0-9][0-9]?)\.){3} 0-9]?)$/!d' > output.txt 6 1785 1.1K III 216K Jackie Singh @HackingButLegal Subscribe Sample geolocations from the first 100 IPs (these are sorted 'low to high', and many Asia-based netblocks start with the number 1) Checking... #: 26/100 74 to go IP Address Reverse DNS Country Region • City Zip Code Timezone ISP 1-172-10-38.dynamic- Penghu | Penghu 1.172.10.38 Taiwan Asia/Taipei Chunghwa Telecom Co., Ltd. ip.hinet.net County County 1-172-15-59.dynamic- Penghu 1.172.15.59 Taiwan ip.hinet.net County | Penghu County Asia/Taipei Chunghwa Telecom Co., Ltd. 1.186.48.26 1.186.48.26 India Karnataka 1.207.26.87 1.207.26.87 China Guizhou 1.23.84.39 1.23.84.39 India West Bengal Kolkata Bengaluru 560056 Asia/Kolkata Guiyang 550000 Asia/Shanghai 700014 Asia/Kolkata DVOIS Chinanet Tikona Infinet Ltd. South 1.234.27.239 1.234.27.239 Seoul Seocho-gu 066 Asia/Seoul SK Broadband Co Ltd Korea 1.24.119.19 1.24.119.19 China Fujian Zhangzhou Asia/Shanghai China Unicom Neimeng Province Network South 1.251.19.135 1.251.19.135 Daegu Seo-gu 418 Asia/Seoul SK Broadband Co Ltd Korea 1.26.102.189 1.26.102.189 China Fujian Zhangzhou Asia/Shanghai China Unicom Neimeng Province Network 1.53.161.195 1.53.161.195 Vietnam Ho Chi Minh | Quan Binh Thanh 1.55.89.216 1.55.89.216 Vietnam Hanoi Hanoi 1.55.95.220 1.55.95.220 Vietnam Hanoi Hanoi 1.59.151.107 1.59.151.107 China Heilongjiang Harbin 1.61.122.87 1.61.122.87 China Heilongjiang Harbin 150000 Asia/Shanghai 1.62.83.6 1.62.83.6 China Heilongjiang Harbin 150000 Asia/Shanghai Asia/Ho Chi Minh FPT Telecom Company Asia/Bangkok Asia/Bangkok 150000 Asia/Shanghai FPT Telecom Company China Unicom Heilongjiang Province Network China Unicom Heilongjiang Province Network China Unicom Heilongjiang Province Network FPT Telecom Company 1-64-176- 1.64.176.95 Hong Kong Eastern 095.static.netvigator.com Heng Fa Chuen Asia/Hong_Kong PCCW IMS Limited 1-64-55- 1.64.55.226 Hong Kong Eastern 226.static.netvigator.com Metropole Building 96521 Asia/Hong_Kong PCCW IMS Limited 12:03 PM ⚫ Jul 10, 2024 250K Views](https://i.kym-cdn.com/photos/images/list/002/859/063/865.png)


Comments ( 36 )
Sorry, but you must activate your account to post a comment.
Please check your email for your activation code.