XZ Backdoor Linux Hack
Part of a series on Linux. [View Related Entries]
This submission is currently being researched & evaluated!
You can help confirm this entry by contributing facts, media, and other evidence of notability and mutation.
| Navigation |
| About • Origin • Spread • Various Examples • Search Interest • External References • Recent Images |
About
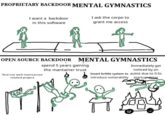
XZ Backdoor Linux Hack refers to the discovery of a malicious "backdoor" in XZ compression tools used in some newer versions of open-source Linux systems. Microsoft engineer Andres Freund found the backdoor in late March 2024 after he noticed a half-second lag while logging into his machine. Further investigation revealed code introduced into the system over the course of two years by a developer named Jia Tan that aimed to grant remote access to every computer running the latest versions of Linux-based operating systems Ubuntu, Fedora and Debian. Engineers and tech enthusiasts shared memes about Freund's discovery, with many jokes leveraging the fact that he was tipped off by a mere 500-millisecond delay in his system.
Origin
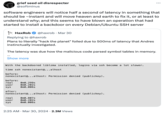
On March 29th, 2024, Microsoft engineer Andres Freund made a post on Mastodon[1] urging people who run "Debian Testing, Unstable, or some other more 'bleeding edge' distribution" to upgrade their Linux systems as soon as possible (seen below). He shared a document about how he discovered a backdoor in the XZ compression tool used in Linux distributions, saying that he was tipped off by a minute lag in his system.

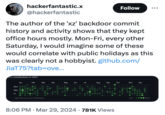
The backdoor commits were allegedly added by a developer known online as Jia Tan over the course of two years, with work logs indicating that their contributions took place at regular weekly intervals as part of a 9-5 job (seen below, left).[3] Moreover, some developers shared on YCombinator[4] that Jia Tan had urged them to add the compromised XZ feature to newer versions of Fedora (seen below, right).

![https://news.ycombinator.com/item?id=39865810#39866275 rwmj 1 day ago | next [-] Very annoying - the apparent author of the backdoor was in communication with me over several weeks trying to get xz 5.6.x added to Fedora 40 & 41 because of it's "great new features". We even worked with him to fix the valgrind issue (which it turns out now was caused by the backdoor he had added). We had to race last night to fix the problem after an inadvertent break of the embargo. He has been part of the xz project for 2 years, adding all sorts of binary test files, and to be honest with this level of sophistication I would be suspicious of even older versions of xz until proven otherwise. reply](https://i.kym-cdn.com/photos/images/newsfeed/002/785/344/a55.png)
Spread
News about Andres Freund's discovery made it to X / Twitter on March 29th, 2024, with X[2][5] user @thegrugq questioning the role of Jia Tan in the hack, saying that it is unlikely that they were an innocent but compromised developer, and adding that the end goal of the hack would have been access to every system running Fedora, Debian and Ubuntu. The post gathered over 5,000 likes in a day (seen below).


On March 30th, Redditors[9] on /r/Linux theorized that the XZ backdoor must have been the work of malicious state actors, with Jia Tan being a pseudonym for an entire team of workers undertaking a long-term state-sponsored campaign (seen below. left). Also on March 30th, Redditor[10] /u/shy_cthulhu posted a Cat Looks Inside meme about he backdoor to /r/linuxmemes, gathering over 800 upvotes in a day.
![XZ Backdoor Linux Hack [-] Mysterious_Focus6144 352 points 17 hours ago The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system(). It sounds like the backdoor attempt was meant as the first step of a larger campaign: 1. Create backdoor. 2. Remotely execute an exploit. 3. profit. This methodical, patient, sneaky effort spanning a couple of years makes it more likely, to me at least, to be the work of a state, which also seems to be the consensus atm permalink source embed save save-RES report reply hide child comments [-] ProgsRS 159 points 16 hours ago It's very likely to be a planned group project given the amount of time it took. Less likely for a lone actor to have this much patience, foresight and commitment. There were others involved as fresh accounts who played different roles (like pressuring the maintainer) during certain periods and suddenly dropped off after, while Jia Tan was a separate persona who had been slowly and separately building trust with the end goal and task of delivering the final payload. It's possible that this was all the same person switching roles, but it's more likely to be an organized group effort over the span of years. permalink source embed save save-RES parent report reply hide child comments](https://i.kym-cdn.com/photos/images/newsfeed/002/785/396/cff.png)

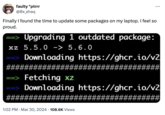
On March 30th, 2024, X[6] user @vxunderground made a post calling Andres Freund the "silver back gorilla of nerds" and the "internet final boss," gathering over 18,000 likes in a day (seen below, left). That same day, X[7] user @0x_shaq joked about installing the compromised software on their system, gathering over 3,000 likes in a day (seen below, right).


Also on March 30th, X[8] user @mippl3 posted a video of Steph Curry discovering a defect in the basketball court because of a failed dribble, writing, "This is explains how the xz backdoor was found," and gathering over 12,000 likes in a day (seen below).
This is explains how the xz backdoor was found pic.twitter.com/n9rNjvawHU
— myq (@mippl3) March 30, 2024
Various Examples





Search Interest
Unavailable.
External References
[1] Mastodon – AndresFreundTec
[3] X – hackerfantastic
[6] X – vxunderground
[10] Reddit – /r/linuxmemes
Recent Videos
There are no videos currently available.
Recent Images 20 total
Share Pin
Related Entries 3 total
Recent Images 20 total
Recent Videos 0 total
There are no recent videos.
![XZ Backdoor Linux Hack [-] Mysterious_Focus6144 352 points 17 hours ago The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system(). It sounds like the backdoor attempt was meant as the first step of a larger campaign: 1. Create backdoor. 2. Remotely execute an exploit. 3. profit. This methodical, patient, sneaky effort spanning a couple of years makes it more likely, to me at least, to be the work of a state, which also seems to be the consensus atm permalink source embed save save-RES report reply hide child comments [-] ProgsRS 159 points 16 hours ago It's very likely to be a planned group project given the amount of time it took. Less likely for a lone actor to have this much patience, foresight and commitment. There were others involved as fresh accounts who played different roles (like pressuring the maintainer) during certain periods and suddenly dropped off after, while Jia Tan was a separate persona who had been slowly and separately building trust with the end goal and task of delivering the final payload. It's possible that this was all the same person switching roles, but it's more likely to be an organized group effort over the span of years. permalink source embed save save-RES parent report reply hide child comments](https://i.kym-cdn.com/photos/images/list/002/785/396/cff.png)









Comments ( 7 )
Sorry, but you must activate your account to post a comment.
Please check your email for your activation code.